JWT Authentication – Json Web Tokens
Hello People, Today we are going to discuss about JWT authentication – Json Web Tokens and how it works.
Securing a website is every developers goal and with http its a bit difficult as it is stateless.
What Is Stateless?
When a sender sends a request to the server, the server processes it and sends back a response to the sender. Then, the cycle is over and the state is closed. The next request, even from the same sender, is considered a new request, or a new state. In short, every request is new to the server.
In this situation, if a sender requests a secured resource, then the sender has to be authenticated and verified , and they should have write permission to access the resource. This is done through the authentication by credentials.
Now, as every request is stateless, is it like we need to send the username/password every time. Yes, it is quite possible but not at all feasible. To deal with this problem, there are many mechanisms that can be used, and one of them is token-based authentication.
What Is Token-Based Authentication?
Whenever a server receives a request with username and password, it generates a token and send it to the user back. When next request is send by the user , instead of sending username and password again to authenticate, he sends the token in header information which is now the source of truth for authentication between cleint and server.
Once the token gets verified againt the user, user gets authenticated to move ahead in the restricted area of website.
There are many tokens based authentication available, a JSON web token (JWT) is one of them.
What Is a JWT Token?
A JSON web token (JWT) is an open standard (RFC 7519) that is a compact and self-contained way for securely transmitting information between systems as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
How JWT works ?
JWT token is normally a JSON object so it has a unique structure to put the information.

Header
This contains 2 information, alogorithm used for signing the token and type of token. Once this object is created, it is encoded with Base64Url to form the first part of the JWT token.

Payload
Payload contains information about the data which server wants to send to client. The second part of the token is the payload, which contains some extra information not mandatory but recommended like :

issmeans the issuing entity, in this case, our authentication serveriatis the timestamp of creation of the JWT (in seconds since Epoch)subcontains the technical identifier of the userexpcontains the token expiration timestamp
Signature
Signature is created by base64 encoded Header, Payload with Secret in the algorithm . This secret is only known to the server.
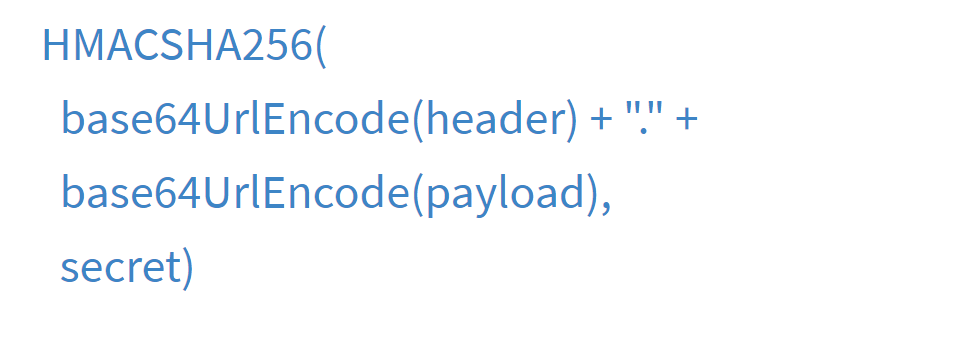
How to validate a JWT signature?
When server receives a JWT token it should have the secret key which is used to create the signature a the first place.
To verify the signature, we simply can take the JWT header plus the payload and hash it together with the password.
And if we get back the same hash as in the signature it means that the token must be valid, because only someone with the password could have come up with that signature.
When Should We Use JWT Authentication?
For Authentication and Authorization and also we can use JWT token in information exchange.
Thanks for reading this article, and I hope this gave you an idea about JWT token-based web authentication. This is a widely adopted approach, and there are lots of libraries available to helps implement JWT with any technology stack.